The Commonwealth Cyber Security Posture in 2022 (the report) informs Parliament on the implementation of cybersecurity measures across the Commonwealth government, for the period January 2021 to June 2022. As of June 2022, the Commonwealth comprised 97 non-corporate Commonwealth entities (NCCEs), 71 corporate Commonwealth entities (CCEs) and 17 Commonwealth companies (CCs).
Executive summary
The Commonwealth Cyber Security Posture in 2022 (the report) informs Parliament on the implementation of cybersecurity measures across the Commonwealth government, for the period January 2021 to June 2022. As of June 2022, the Commonwealth comprised 97 non-corporate Commonwealth entities (NCCEs), 71 corporate Commonwealth entities (CCEs) and 17 Commonwealth companies (CCs). Throughout this report, the term ‘entities’ refers to all NCCEs, CCEs and CCs combined.
For the purposes of this report, an entity’s cybersecurity posture comprises the following four dimensions:
- Cybersecurity hardening: the entity’s implementation of cybersecurity mitigations, primarily the Essential Eight mitigation strategies, to reduce the likelihood of an information communications technology (ICT) system being compromised.
- Incident preparedness and response: the entity’s readiness to respond to cybersecurity incidents.
- Leadership and planning: the entity’s leadership engagement with cybersecurity to support a strong cybersecurity culture.
- Cyber defence services: the entity’s engagement with cyber defence services that detect and stop malicious cyber activity before it can impact a network.
The data included in this report is primarily derived from the ASD Cyber Security Survey for Commonwealth Entities. The Australian Signals Directorate (ASD) surveys entities annually regarding their cybersecurity practices. The survey addresses entities’ implementation of the Essential Eight Maturity Model; leadership and culture; incident management; and engagement with ASD services. NCCEs are required to respond to the survey under Policy 5: Reporting on Security of the Protective Security Policy Framework (PSPF); all other entities are encouraged to respond. This year, 92% of entities participated in the survey. This data was supplemented by information collected by ASD in the performance of its duties.
At various points in this report, reference is also made to relevant findings from the Protective Security Policy Framework Assessment Report 2020–21 (hereafter referred to as the PSPF Assessment Report), published by the Attorney-General’s Department (AGD). Each financial year, NCCEs must report on their security posture to AGD, with particular reference to implementation of government policies under the PSPF. The PSPF Assessment Report is an aggregated assessment of these findings. That report provides assurance to government and the Australian public that entities are implementing security measures that proportionately address their unique security risk environments.
The findings presented here indicate that the cybersecurity posture across the Commonwealth is well-established in some areas but requires improvement in others. Specifically:
- Essential Eight maturity levels improved, but remain low, across the Commonwealth.
- The proportion of entities that have reached Overall Maturity Level 2 through implementation of Essential Eight controls alone increased from 4% in 2021 to 11% this year.
- The proportion of entities that self-assessed as having reached Maturity Level 2 when compensating controls are taken into account increased from 14% in 2021 to 19% this year.
- Most entities had prepared for a cybersecurity incident and were ready to respond as needed. However, the number of entities that had exercised their Incident Response Plan every two years, and the number of entities reporting incidents to the Australian Cyber Security Centre (ACSC), was relatively low.
- 79% of entities had an Incident Response Plan; however only 49% of entities exercised their Incident Response Plan at least every two years.
- 80% of entities reported at least 80% of cybersecurity incidents to their senior management.
- 47% of entities reported 20% or fewer cybersecurity incidents to the ACSC.
- In 2021–22, entities reported 255 cybersecurity incidents to the ACSC, accounting for 23% of all cybersecurity incidents reported.
- There was a general improvement in cybersecurity leadership and planning across the Commonwealth. However, improvements could be made regarding entities’ delivery of cybersecurity training to their workforces.
- 72% of entities had a cybersecurity strategy, up from 61% in 2021.
- 68% of entities provided cybersecurity training for their workforce at least annually.
- 34% of entities provided privileged user training at least annually.
- Engagement with ASD’s cyber defence services is low to moderate.
- 2% of entities have joined the Cyber Threat Intelligence Sharing (CTIS) platform.
- 26% of entities were using the Australian Protective Domain Name System (AUPDNS).
- 38% of entities were protected by the Domain Takedown Service.
Against this backdrop, the ACSC will help entities improve their cybersecurity posture. The ACSC will seek to:
- increase the number of entities engaging with the Cyber Maturity Measurement Program (CMMP) and ACSC Cyber Security Uplift Services for Government (ACSUSG)
- support entities to establish and exercise an Incident Response Plan
- investigate why some entities report a low percentage of incidents to the ACSC, and identify remediation measures
- encourage improved rates of annual cybersecurity workforce training across the Commonwealth
- increase the number of entities utilising CTIS, AUPDNS and the Domain Takedown Service.
1. Introduction
Improving the cybersecurity of Australia’s public, private and civil sectors is a priority of the Australian Government. As Australians increasingly rely on the internet and internet-connected devices, the scale of cyber risk continues to grow. Throughout the past year, Australia was the target of malicious cyber actors who, through persistent cyber operations, put Australia’s security, stability and prosperity at risk.
The Australian Government plays an important role in monitoring, shaping and enabling cybersecurity across the economy. In particular:
- ASD – through the ACSC – provides cybersecurity advice and assistance to Australian governments at the federal, state, territory and local levels, business and critical infrastructure, as well as communities and individuals.
- The Department of Home Affairs (Home Affairs) leads Australia’s national cybersecurity policy and strategy, driving cybersecurity policy improvements across government and industry.
- AGD manages the PSPF, which sets out government protective security policy and supports entities to effectively implement that policy.
- The Digital Transformation Agency (DTA) drives digital transformation across government by providing strategic and policy leadership, and investment advice and oversight.
Within this context, entities – that is, the Australian Government’s own departments and agencies – are responsible for maintaining the cybersecurity of their data and networks. Specifically, each entity is responsible for the security of its own ICT systems pursuant to the Public Governance, Performance and Accountability Act 2013 (PGPA Act). Under the PSPF, an entity’s accountable authority must approve an appropriate security plan to manage security risks.
This report provides an assessment of the cybersecurity posture of entities as at 30 June 2022, covering progress made by entities from 1 January 2021. It is the third report prepared in response to the Joint Committee of Public Accounts and Audit's Report 467: Cybersecurity Compliance published in October 2017, which recommended that ASD and AGD report to Parliament annually on the cybersecurity posture of the Commonwealth. The annual reports are intended to support increased transparency in cybersecurity reporting.
1.1 Key findings of this report
The data included in this report is primarily derived from the annual ASD Cyber Security Survey for Commonwealth Entities. NCCEs are required to respond to the survey under Policy 5: Reporting on Security; all other entities are encouraged to respond. This year, 92% of entities participated in the survey. This data was supplemented by information collected by ASD in the performance of its duties.
At various points in this report, reference is also made to relevant findings from the PSPF Assessment Report, published by AGD. Each financial year, NCCEs must report on their security posture to AGD, with particular reference to the implementation of government policies under the PSPF. The PSPF Assessment Report is an aggregated assessment of these findings. That report provides assurance to government and the Australian public that entities are implementing security measures that proportionately address their unique security risk environments.
Insight into the cybersecurity posture of individual entities may increase their risk of being targeted by adversaries. As such, this report does not identify entities by name. Instead, all data has been anonymised. Only aggregated results are provided.
For the purposes of this report, an entity’s cybersecurity posture comprises four dimensions:
- Cybersecurity hardening: the implementation of cybersecurity mitigations – primarily the Essential Eight mitigation strategies – to reduce the likelihood of an entity’s ICT systems being compromised.
- Incident preparedness and response: the entity’s readiness to respond to cybersecurity incidents.
- Leadership and planning: the entity’s leadership engagement with cybersecurity, to support a strong cybersecurity culture.
- ASD cyber defence services: the entity’s engagement with cyber defence services that serve to detect and stop malicious cyber activity before it can impact a network.
The findings presented here indicate that the cybersecurity posture across the Commonwealth is well-established in some areas, but requiring improvement in others. Specifically:
- Essential Eight maturity levels remained low, though improving, across the Commonwealth.
- Most entities had prepared for a cybersecurity incident and were ready to respond as needed. However, the number of entities that had exercised their Incident Response Plan every two years, and the number of entities reporting incidents to the ACSC, was relatively low.
- There was a general improvement in cybersecurity leadership and planning across the Commonwealth; most entities had a cybersecurity strategy. However, improvements could be made with regard to entities’ delivery of cybersecurity training to their workforces.
- Engagement with ASD’s cyber defence services is low to moderate.
The remainder of this report provides more detail on these findings and outlines next steps for improvement.
- Section 2 outlines findings relating to the Commonwealth’s implementation of technical controls to defend entities’ ICT environments against cybersecurity threats.
- Section 3 outlines findings relating to entities’ planning and preparedness to respond to adverse cybersecurity incidents.
- Section 4 outlines findings regarding the leadership and planning that underpins entities’ cybersecurity culture.
- Section 5 outlines findings regarding entities’ adoption of cyber defence services provided by ASD.
- Finally, Section 6 summarises the key findings and offers next steps in the improvement of the Commonwealth cybersecurity posture.
2. Cybersecurity hardening
The implementation of cybersecurity controls helps entities defend their ICT environments against a range of threats, thereby avoiding costly remediation, downtime and lost productivity, and loss of public confidence. In relation to network hardening, the cybersecurity posture of entities was assessed using two data sets:
- Responses to the ASD Cyber Security Survey for Commonwealth Entities, where entities report whether they have implemented controls recommended by the Essential Eight Maturity Model. Based on those responses, ASD calculates the entities’ maturity level.
- Cyber Hygiene Improvement Programs (CHIPs) results. CHIPs is an open-source intelligence capability that uses objective and data-driven approaches to detect external indicators of network vulnerability.
2.1 Essential Eight Maturity Model
The ACSC’s Essential Eight Maturity Model outlines a set of mitigation strategies to help organisations reduce their likelihood of experiencing a cybersecurity incident, and the impact of the incident if they do.
In 2020, ASD conducted a review of the Essential Eight to ensure that it remained contemporary and contestable. This review was based on the Essential Eight assessments carried out across the Commonwealth, engagement with government entities to understand their experiences implementing the Essential Eight, and awareness of the constantly evolving cyberthreat environment. In July 2021, the updated Essential Eight Maturity Model was published on cyber.gov.au.
2.1.1 Implementation of the Essential Eight Maturity Model
The Essential Eight Maturity Model comprises four maturity levels (Maturity Levels 0 to 3). The higher levels of maturity protect entities against moderate-to-high degrees of sophistication in adversary tradecraft and targeting. As of July 2022, it is a core requirement of the PSPF that entities implement the Essential Eight strategies to at least Maturity Level 2. A network’s Overall Maturity Level is equal to its least mature strategy.
The Essential Eight Maturity Model comprises the following eight strategies:
- Application control: ensures only corporately approved software applications can be executed on a computer, protecting against the execution of malicious applications.
- Patch applications: applying vendor patches or other vendor mitigations prevents known vulnerabilities in applications from being exploited.
- Configure Microsoft Office macro settings: limits macro programs embedded in Microsoft Office files from executing, thereby preventing potential malicious activity.
- User application hardening: limits the use of potentially exploitable user application functionality to only what is required, and removes particularly vulnerable software altogether.
- Restrict administrative privileges: limits the unnecessary provision of administrative privileges, reducing the potential for these to be exploited by adversaries to gain full access to computers and data.
- Patch operating systems: applying vendor patches or other vendor mitigations prevents known vulnerabilities in operating systems from being exploited.
- Multi-factor authentication: requires users to present multiple authentication credentials to log in, rather than just using a passphrase, thereby preventing adversaries logging in as a user if they know the user’s passphrase.
- Regular backups: making a copy of data, software and configuration settings, storing it securely and periodically testing the ability to restore it, enables data and computers to be restored after an incident such as ransomware or computer hardware failure.
The Essential Eight Maturity Model recommends that organisations implement the Essential Eight using a risk-based approach. Where strategies cannot be implemented, these exceptions should be minimised and compensating controls used to manage the resulting risk. If the gap is effectively mitigated, the entity may self-assess that they have achieved maturity against that strategy.
2.1.2 Level of Essential Eight implementation by entities
The vast majority of entities have not implemented all the Essential Eight mitigation strategies to Maturity Level 2. Specifically:
- Only 11% of entities had reached Overall Maturity Level 2, relying on the implementation of Essential Eight controls alone; an increase from 4% in 2021.
- 19% of entities self-assessed that they had reached Maturity Level 2 when compensating controls to mitigate gaps in the Essential Eight implementation were taken into account; an increase from 14% in 2021.
- Between 2021 and 2022, the greatest improvements to the number of entities implementing an Essential Eight strategy to Maturity Level 2 were observed in Patch applications (26% improvement) and Patch operating systems (24% improvement) (Figure 1).
- Regular backups, Application control and Patch operating systems were implemented to Maturity Level 2 by the highest proportion of entities, following the application of compensating controls (Figure 2).
- User application hardening and Restrict administrative privileges were implemented to Maturity Level 2 by the lowest proportion of entities, following the application of compensating controls (Figure 2).
2.1.3 Protective Security Policy Framework Report 2020–21
The PSPF Assessment Report includes reporting against Policy 10: Safeguarding data from cyberthreats. In 2020–21, this policy mandated the implementation of four of ASD’s Essential Eight mitigation strategies: Application control, Patch applications, Restrict administrative privileges, and Patch operating systems.
The PSPF Assessment Report found that 28% of entities had implemented these strategies to a ‘Managing’ or ‘Embedded’[1] level.
From July 2022, the PSPF requires entities to implement Maturity Level 2 for each of the Essential Eight strategies.
Figure 1: Percentage of entities with Essential Eight Maturity Level 2 or higher (Essential Eight strategies only)
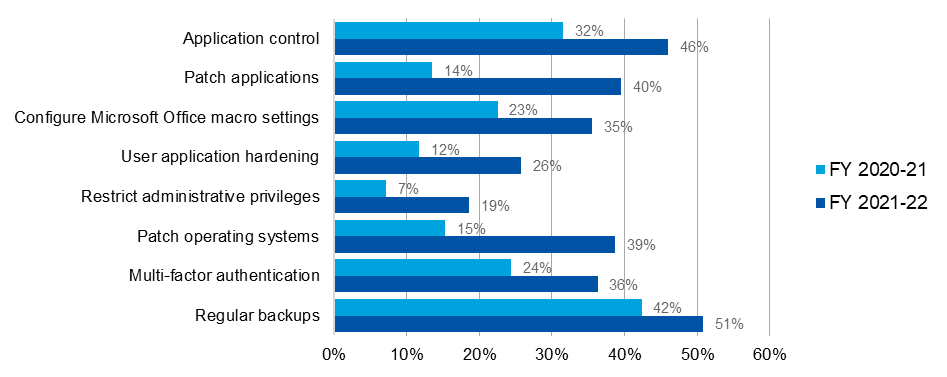
| Figure 1 | FY 2020-21 | FY 2021-22 |
|---|---|---|
| Application control | 32% | 46% |
| Patch applications | 14% | 40% |
| Configure Microsoft Office macro settings | 23% | 35% |
| User application hardening | 12% | 26% |
| Restrict administrative privileges | 7% | 19% |
| Patch operating systems | 15% | 39% |
| Multi-factor authentication | 24% | 36% |
| Regular backups | 42% | 51% |
Figure 2: Percentage of entities with Essential Eight Maturity Level 2 or higher (Essential Eight plus compensating controls)
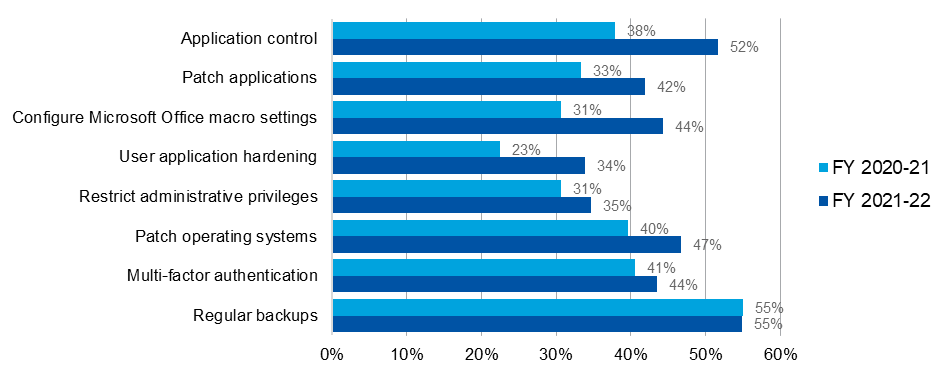
| Figure 2 | FY 2020-21 | FY 2021-22 |
|---|---|---|
| Application control | 38% | 52% |
| Patch applications | 33% | 42% |
| Configure Microsoft Office macro settings | 31% | 44% |
| User application hardening | 23% | 34% |
| Restrict administrative privileges | 31% | 35% |
| Patch operating systems | 40% | 47% |
| Multi-factor authentication | 41% | 44% |
| Regular backups | 55% | 55% |
2.2 Cyber Hygiene Improvement Programs scanning (CHIPs)
CHIPs scans provide information to entities on a range of cyber hygiene indicators, identifying areas of cybersecurity concern. Over the reporting period, the proportion of domains protected by key security measures increased, while the number of domains hosting dormant websites decreased. Specifically, between February 2021 and May 2022:
- use of recommended email security[2] rose from 8.0% to 61.3%
- use of recommended email encryption[3] rose from 17.9% to 41.6%
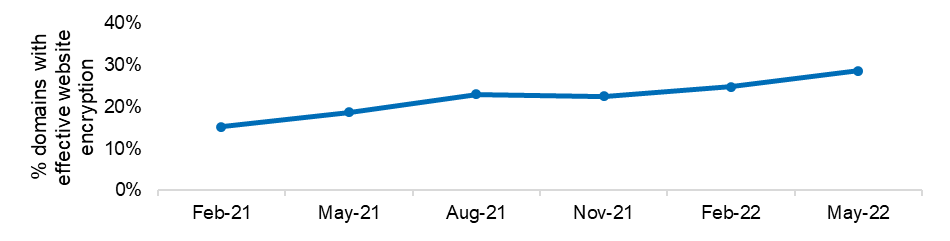
- use of recommended web server encryption[4] rose from 15.2% to 28.6%
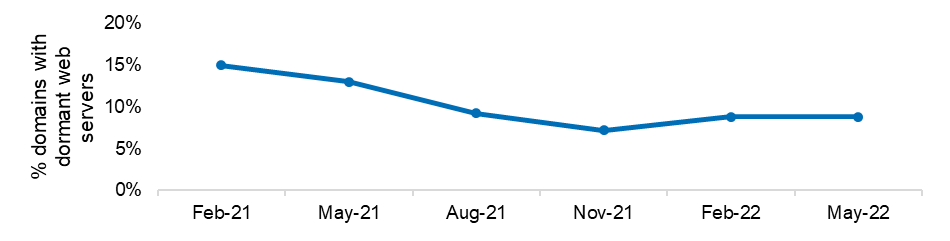
- the existence of dormant websites (which might be used to host or launch malicious activity) decreased from 15.0% to 8.8%.
These results are further described in Figure 3 to Figure 6.
CHIPs reporting indicates that entities are improving their overall implementation of the security protocols above. However, the proportion of Commonwealth domains in which these cyber hygiene measures have not been effectively implemented remains high.
Case Study 1: Support to the 2021 Census
In August 2021, the Australian Bureau of Statistics (ABS) ran the eighteenth Census of Population and Housing (Census) in Australia. From planning through to delivery, ASD provided ABS with cybersecurity advice, assistance and technical uplift to help ensure the cybersecurity of the Census and its data.
Prior to the Census, ASD provided ABS with cybersecurity advice for its procurement process, a cybersecurity maturity assessment across ABS networks, a review of the platform hosting the Census, and threat intelligence briefings. ASD employed its cyber defence service capabilities to assess and pre‑empt malicious cyber activity against the Census.
Throughout the Census, ASD was in constant communication with ABS and conducted passive monitoring of the ABS systems and incident response support to help detect and respond to threats. On Census night, ASD provided on-site operational support to bolster any critical incident response.
ASD found no indication of malicious activity through its assessments, and critical cybersecurity recommendations were resolved by ABS prior to the Census. The 2021 Census was completed successfully without cybersecurity incident.
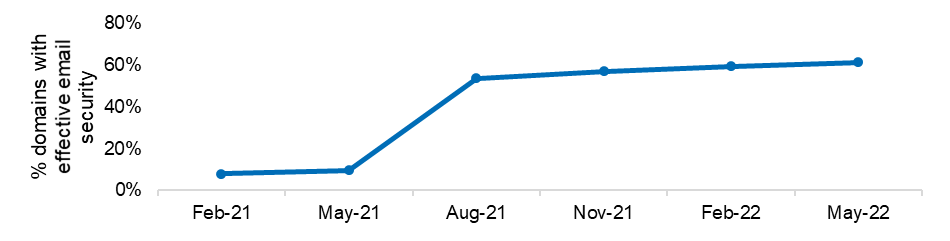 Figure 3: Implementation of email security measures across entities’ domains
Figure 3: Implementation of email security measures across entities’ domains
| Figure 3 | % domains with effective email security |
|---|---|
| Feb-21 | 8.0% |
| May-21 | 9.7% |
| Aug-21 | 53.6% |
| Nov-21 | 57.0% |
| Feb-22 | 59.4% |
| May-22 | 61.3% |
Figure 4: Implementation of email encryption by device across entities’ domains
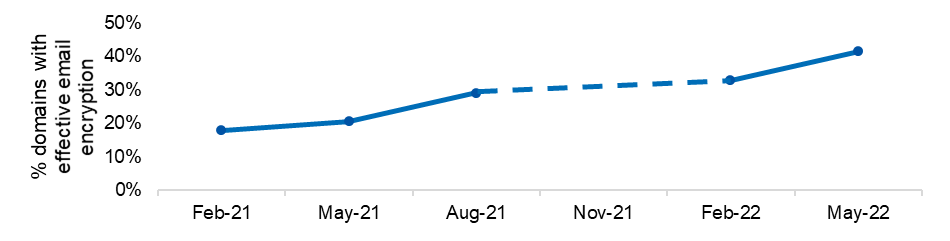
| Figure 4 | % domains with effective email encryption |
|---|---|
| Feb-21 | 17.9% |
| May-21 | 20.6% |
| Aug-21 | 29.2% |
| Nov-21 | - |
| Feb-22 | 32.7% |
| May-22 | 41.6% |
Figure 5: Implementation of website encryption across entities’ domains
| Figure 5 | % domains with effective website encryption |
|---|---|
| Feb-21 | 15.2% |
| May-21 | 18.6% |
| Aug-21 | 22.9% |
| Nov-21 | 22.5% |
| Feb-22 | 24.7% |
| May-22 | 28.6% |
Figure 6: Dormant websites across entities’ domains
| Figure 6 | % domains with dormant web servers |
|---|---|
| Feb-21 | 15.0% |
| May-21 | 13.0% |
| Aug-21 | 9.2% |
| Nov-21 | 7.2% |
| Feb-22 | 8.8% |
| May-22 | 8.8% |
3. Incident preparedness and response
A cybersecurity event occurs when a system, service or network flags a possible breach of security policy, failure of safeguards or a previously unknown situation that may be relevant to security. A cybersecurity incident is an unwanted or unexpected cybersecurity event, or a series of such events, that have a significant probability of compromising business operations.
Cybersecurity incidents may result in the denial of access to, the theft of, or the destruction of systems and data. If not effectively managed, a cybersecurity incident may undermine public confidence in an organisation, and the incident’s remediation may consume significant resources.
While it is important to defend against cybersecurity incidents, it is impossible to avoid them entirely. Entities should plan for, and prepare to respond to, cybersecurity incidents. This includes identifying the data and systems essential to their business, accounting for cybersecurity incidents in business continuity planning, and developing and exercising an incident response plan.
Reporting cybersecurity incidents is also essential to ensure that they are dealt with appropriately and that any impact is considered fully. According to Policy 5: Reporting on security, entities are required to report ‘significant or reportable’ cybersecurity incidents to the ACSC.
Entities are a common target for malicious cyberactivity. In 2021–22, entities reported 255 cybersecurity incidents to the ACSC, accounting for 23% of all cybersecurity incidents reported.
3.1 Levels of incident preparedness and reporting
In relation to incident preparedness and response, the cybersecurity posture of entities is assessed using responses from the ASD Cyber Security Survey for Commonwealth Entities. Specifically, entities respond to a series of questions designed to assess their level of preparedness to respond to a cybersecurity incident, and their incident reporting behaviour.
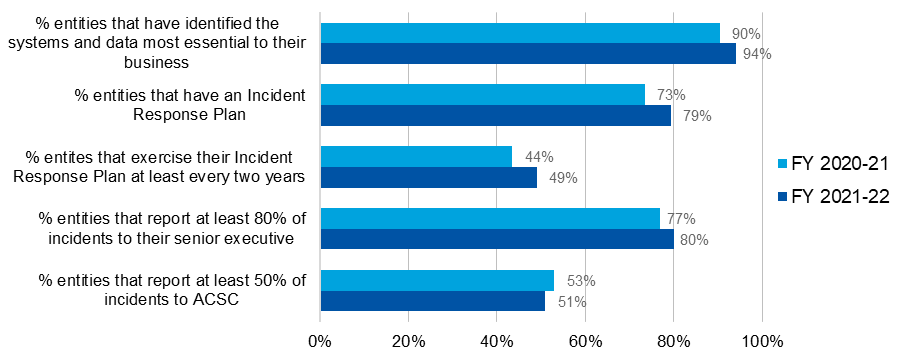
Findings indicate that the majority of entities had planned for a cybersecurity incident, and were ready to respond, if needed. However, a much smaller proportion of entities had exercised their Incident Response plan. Specifically, as shown in Figure 7:
- 94% of entities had identified the systems and data most essential to their business; an increase from 90% in 2021.
- 79% of entities had an Incident Response Plan; an increase from 73% in 2021.
- 49% of entities exercised their Incident Response Plan at least every two years; an increase from 44% in 2021.
Notably, there was little change in these results between 2021 and 2022.
Figure 7: Indicators of entities' incident preparedness and response
| Figure 7 | FY 2020-21 | FY 2021-22 |
|---|---|---|
| % entities had identified the systems and data most essential to their business | 90% | 94% |
| % entities had an Incident Response Plan | 73% | 79% |
| % entities exercised their Incident Response Plan at least every two years | 44% | 49% |
| % entities that report at least 80% of incidents to their senior executive | 77% | 80% |
| % entities that report at least 50% of incidents to ACSC | 53% | 51% |
While most entities report a high rate of cybersecurity incidents to their senior management, this is not the case with regard to reporting incidents to the ACSC. Rather, a large cohort of entities report all cybersecurity incidents to the ACSC, while a distinct cohort report relatively few cybersecurity incidents to the ACSC. As shown in Figure 7:
- 80% of entities reported at least 80% of the incidents observed on their network to their senior management; an increase from 77% in 2021.
- 51% of entities reported at least 50% of incidents observed on their network to the ACSC, a minor decrease from 53% in 2021:
- 41% reported 100% of incidents observed on their network to the ACSC, increasing from 39% of entities in 2021.
- 47% reported 20% or fewer incidents observed on their network to the ACSC, increasing from 45% in 2021.
- 12% reported between 30% and 90% of incidents observed on their network to the ACSC, down from 16% in 2021.
Under Policy 5: Reporting on security, entities are required to report ‘significant or reportable’ cybersecurity incidents to the ACSC. The low rate of incident reporting may have a variety of causes. Specifically:
- A proportion of entities may be experiencing a high number of low-impact incidents that do not meet the reporting threshold.
- A proportion of entities may be experiencing reportable incidents, but do not recognise them as reportable.
Case Study 2: Log4j vulnerability response
The Log4j vulnerabilities were the most prevalent critical vulnerabilities in the 2021–22 financial year. On 10 December 2021, ASD issued a public alert, and commenced awareness and response initiatives to mitigate the potential compromise. Due to its widespread use in popular software and hardware platforms, over 100,000 products may contain Log4j.
Between December 2021 and January 2022, ASD provided technical support to impacted organisations, releasing 2 Alerts and 2 Advisories flagging the active exploitation. ASD also provided technical advice and guidance for mitigation and detection, hosted 7 information sharing events through the ACSC Partnership Program, and amplified advice on social media, which had a potential reach of over 1 million people. On 22 December 2021, ASD also released a joint public technical advisory on mitigations for Log4j-related vulnerabilities with the US, UK, Canada and New Zealand.
ASD is aware of malicious actors conducting a large number of reconnaissance scans for Log4j vulnerabilities. Some Australian networks were compromised through Log4j vulnerabilities, and ASD responded to over 50 cybersecurity incidents. ASD has identified Log4j exploits being used months after the initial disclosure. Log4j is likely to be a means of access for malicious actors for years to come.
Case Study 3: AquaEx
AquaEx, the national cybersecurity exercise series coordinated by ASD in partnership with Australian critical infrastructure owners and operators, was held in August 2021. The exercise brought together Australia’s urban water and wastewater sector and government agencies, with the aim of strengthening industry and government coordinated response to cyber incidents affecting the sector.
The exercise was an opportunity for participants to reflect on existing communication and cooperation arrangements to respond to a cyber incident affecting industry, and how these arrangements can be improved. It enabled industry and government to clarify their roles and responsibilities, including reporting responsibilities for organisations affected by a cyber incident.
AquaEx involved over 14 months of planning, 50 one-on-one planning conferences, 16 exercise management workshops, 4 information sessions, and the development of a Cyber Incident Response Plan template to assist organisations in developing and updating their cyber incident response plans in preparation for the exercise.
Despite the challenges presented by COVID-19 lockdowns, the exercise had a record number of participants. In total, more than 750 participants, from 48 organisations (including four entities), took part in the activity, strengthening relationships and enhancing cyber awareness.
4. Leadership and planning
Strong leadership is essential in setting and maintaining a strong cybersecurity culture, and ensuring cybersecurity remains part of an organisation’s planning and everyday business. In particular, the Chief Information Security Officer (CISO) plays a key role in setting the strategy and direction of an entity’s cybersecurity program. CISOs are typically responsible for providing strategic guidance to their entity’s cybersecurity program and ensuring compliance with cybersecurity policy, standards, regulations and legislation.
The broader workforce also plays a key part in maintaining cybersecurity, and entities should provide ongoing cyber security awareness training to all personnel to help them to understand their security responsibilities.
4.1 Levels of leadership and planning
In relation to leadership and planning, the cybersecurity posture of entities was assessed through a series of questions designed to provide indications of their entity’s cybersecurity leadership, planning and overall culture.
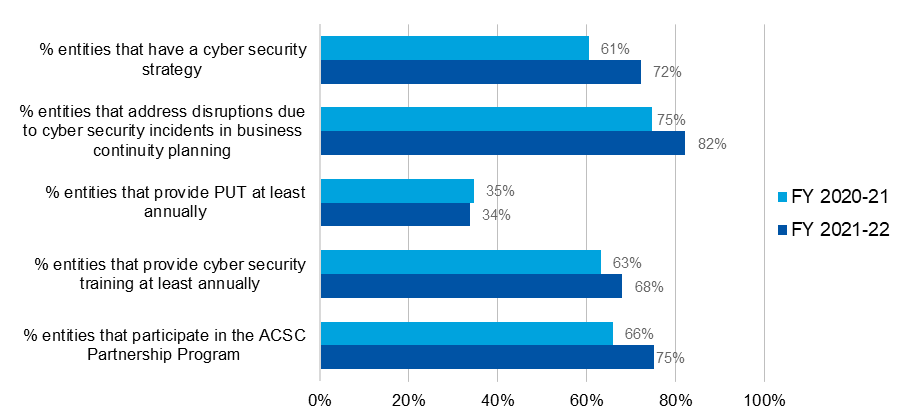
Responses showed improvement on most indicators of leadership and planning (Figure 8). Specifically, as of June 2022:
- 72% of entities had a cybersecurity strategy, up from 61% in 2021.
- 82% of entities addressed cybersecurity incidents in business continuity planning, up from 75% in 2021.
- 68% of entities provided cybersecurity training for their workforce at least annually, increasing from 63% in 2021.
- 75% of entities participated in the ACSC Partnership Program, increasing from 66% in 2021.
Ideally, all entities should engage in these activities. However, the increasingly high uptake across entities signals a general improvement in posture.
A notable exception is cybersecurity training. Responses indicate that 68% of entities provide cybersecurity training to their workforce at least annually, while 34% of entities provided privileged user training (PUT) to ICT users with elevated privileges at least annually.
Figure 8: Indicators of entities' leadership and planning
| Figure 8 | FY 2020-21 | FY 2021-22 |
|---|---|---|
| % entities that have a cybersecurity strategy | 61% | 72% |
| % entities that address disruptions due to cybersecurity incidents in business continuity planning | 75% | 82% |
| % entities that provide PUT at least annually | 35% | 34% |
| % entities that provide cybersecurity training at least annually | 63% | 68% |
| % entities that participate in the ACSC Partnership Program | 66% | 75% |
Case Study 4: Ransomware - Exercise Blue Dawn
Ransomware is one of the most disruptive threats to Australian organisations. In April 2022, ASD coordinated Exercise Blue Dawn, a simulated ransomware cybersecurity incident, for its Network Partners within the ACSC Partnership Program. The exercise supported participants from a range of sectors to clearly identify their strengths and weaknesses, and improved their holistic organisational responses to ransomware.
The 62 participating entities stated that they learned from each other’s expertise and experiences with ransomware, incident response and planning. Conducting cybersecurity exercises such as this are an integral part of cybersecurity preparedness, where relevant personnel or organisations come together in a simulated environment to discuss, review and develop response plans, policies, and capabilities.
As a result of the exercise, participants indicated that they would review and further develop their organisations’ incident response and preparedness plans. In addition, 98% agreed that Blue Dawn enhanced their ability to perform their roles under similar circumstances and that their participation was appropriate and beneficial to their roles. The ACSC continues to develop close collaboration opportunities for ACSC Network Partners to build cyber resilience and maturity for all Australian organisations.
Case Study 5: Australian Protective Domain Name System (AUPDNS)
AUPDNS enhances the security of government networks by blocking connections to malicious websites that may contain ransomware, malware and other cyberthreats. ASD and its industry partner make this service available to all federal, state and territory governments. AUPDNS has proven to be invaluable for threat detection and intelligence gathering, as well as for disrupting or deterring cyberattacks at the reconnaissance phase.
Since the AUPDNS pilot began in March 2020, ASD has analysed abnormal Domain Name Service (DNS) traffic flows to detect possible malicious activity and, through this, either mitigate or reduce the harm of an intrusion for entity customers. AUPDNS has become the largest contributor of indicators of compromise to ASD’s CTIS platform, providing over 80% of CTIS inputs.
During the reporting period, AUPDNS processed more than 30 billion queries and blocked more than 20 million connections to known malicious domains. By the end of the 2021–22 financial year, 49 entities were using the service. As more entities connect to AUPDNS, ASD achieves greater cyberthreat visibility and defence.
5. Cyber defence services
The cyber defence services offered to entities by ASD are designed to detect and stop malicious cyber activity before it can impact organisations or the community. Cyber defence services are intended to tackle the high-volume attacks that affect many targets, from government entities to individual internet users, rather than highly sophisticated and targeted attacks. As such, these services are generally scalable and designed to block malicious cyber activity while in train. It is recommended that all entities take advantage of cyber defence services, either by accessing those provided by ASD or engaging a commercial service.
5.1 ASD services available to entities
ASD provides cyber defence services to entities to mitigate low-sophistication attacks before they impact the network, including:
-
Cyber Threat Intelligence Sharing (CTIS)
In November 2021, ASD began operating the new CTIS platform. CTIS allows participating entities to share observable indicators of compromise (IOCs) at machine speed. Participating organisations can then use these IOCs to identify activity on their own networks. The CTIS platform also allows participating organisations to bi-directionally share IOCs observed on their own networks with other CTIS partners. Since its launch, 28,000 IOCs have been shared on CTIS.
-
Australian Protective Domain Name System (AUPDNS)
The AUPDNS uses threat intelligence to build a block list of known and assessed malicious web domains. These domains are often used to distribute malware, as part of malicious command-and-control channels, or as part of a data-exfiltration channel. AUPDNS prevents devices on subscribed networks from accessing the malicious domains on the block list, thereby interrupting potential malicious activity. Between 1 January 2021 and 30 June 2022, more than 20 million malicious domain requests were blocked by AUPDNS.
-
Domain Takedown Service
The Domain Takedown Service prevents malicious resources from being hosted on unsuspecting entities’ web domains. The service detects potentially malicious activity that is using subscribed entities’ web domains, verifies that this activity is malicious, and issues a takedown notification request to the Domain Host (i.e. the internet service that manages that domain). The majority of takedown notifications are automatically initiated within one minute of identification. Within the reporting period, 70,000 domain takedown notifications were sent to entities.
5.2 Uptake of ASD’s cyber defence services
The uptake of ASD’s cyber defence services was assessed using information collected by ASD as part of their normal operations. According to ASD records, as of 30 June 2022:
- 2% of entities had joined the CTIS platform
- 26% of entities were using AUPDNS
- 38% of entities were protected by the Domain Takedown Service.
6. Conclusion and next steps
Cybersecurity must be a priority for all entities. The findings presented in this report indicate that the cybersecurity posture across the Commonwealth is well-established in some areas, but requiring improvement in others. In particular:
- Most entities do not meet the minimum requirements for cybersecurity, as described in the Essential Eight Maturity Model. This conclusion is supported by the PSPF Assessment Report.
- Most entities had prepared for a cybersecurity incident, and were ready to respond as needed. However, the number of entities that had exercised their Incident Response Plan every two years, and the number of entities reporting incidents to the ACSC, was relatively low.
- There was a general improvement in cybersecurity leadership and planning across the Commonwealth. However, further improvements could be made with regard to entities’ delivery of cybersecurity training to their workforces.
- Engagement with ASD’s cyber defence services is low to moderate across the Commonwealth.
6.1 Next steps
Against this backdrop, entities should work to:
- prioritise, and appropriately resource, improvements to their cybersecurity posture in line with the Essential Eight
- establish and exercise an effective cybersecurity Incident Response Plan
- review their cybersecurity incident reporting practices
- provide annual cybersecurity training and privileged user training across their workforce
- seek to engage with ASD’s cyber defence services.
The ACSC will help entities to improve their cybersecurity posture. The ACSC will:
- increase the number of entities engaging with the Cyber Maturity Measurement Program (CMMP) and ACSC Cyber Security Uplift Services for Government (ACSUSG)
- support entities to establish and exercise an Incident Response Plan
- investigate why some entities report a low percentage of incidents to the ACSC, and identify remediation measures
- encourage improved rates of annual cybersecurity workforce training across the Commonwealth
- increase the number of entities utilising CTIS, AUPDNS and the Domain Takedown Service.
6.2 Final comments
The importance of effective cybersecurity will continue to grow as the Commonwealth government increasingly relies on the internet and internet-connected devices. Entities continue to improve their cybersecurity posture. However, considerable improvement is still required to meet the rapidly evolving cyberthreat environment.
6.3 Report to Parliament 2023
The Commonwealth Cyber Security Posture in 2023 Report to Parliament will be delivered in November 2023. This report will focus on the 2022–23 financial year.
ANNEX A: ASD Services for Commonwealth entities
Cybersecurity hardening
|
From 1 January 2021 to 30 June 2022… 1 678 11 22 212 Quarterly 62 |
Technical publicationsASD publishes the Information Security Manual (ISM), the Essential Eight Maturity Model, and the Strategies to Mitigate Cybersecurity Incidents, all of which outline the technical strategies and controls designed to defend against cyberthreats. ASD also publishes additional guidance on topics of particular relevance, such as cloud and gateway services. Cyber Maturity Measurement Program (CMMP)ASD’s CMMP works with entities to assess their networks’ implementation of the Essential Eight mitigation strategies and their broader cybersecurity posture. Entities are provided with a snapshot of their networks’ cybersecurity posture and tailored advice and recommendations to improve. ACSC Cyber Security Uplift Services for Government (ACSUSG)ASD’s ACSUSG service provides entities with skilled ICT professionals to implement security controls and provide further recommendations aligned with the ACSC’s findings and advice provided through complementary offerings. Information Security Registered Assessors Program (IRAP)Through the IRAP, ASD endorses suitably qualified professionals to provide cybersecurity services to support broader industry and Australian Government. IRAP assessors can provide security assessments of ICT systems, cloud services and gateways. Active Vulnerability Assessments (AVA)AVA is ASD’s ‘red team’ capability, designed to assess the network and system security of Australia’s most critical, nationally significant and sophisticated infrastructure. Cyber Hygiene Improvement Programs (CHIPs)CHIPs uses open source techniques to measure the cyber posture and hygiene of government internet-facing systems and assets. It uses objective and data-driven approaches to detect external indicators that a network may be vulnerable to exploitation. CHIPs provides quarterly reports to Commonwealth, state, territory and local government entities, detailing vulnerability posture and findings for each entity. High-Priority Operational Tasking Cyber Hygiene Improvement Programs (HOT CHIPs)ASD’s HOT CHIPs scans identify network and system vulnerabilities relating to high-priority threats. These scans build ACSC visibility of the government attack surface, and help network owners to build cyber hygiene quickly by providing timely and actionable threat intelligence. Host Based Sensor Program (HBS)ASD’s HBS program provides visibility of the cybersecurity posture of Australian Government ICT systems by collecting telemetry data from government devices. This enables ASD to help entities identify weaknesses and detect intrusions on their ICT infrastructure, and mitigate the consequences of compromise. |
Incident preparedness and response
|
From 1 January 2021 to 30 June 2022… 67 55 3 30 20 3548 |
Alerts and AdvisoriesASD publishes alerts and advisories to cyber.gov.au to inform Australians on cybersecurity threats. Individuals may subscribe to the ACSC Alert Service to have such alerts forwarded to them automatically. Cybersecurity HotlineThe Australian Cybersecurity Hotline ‘1300 CYBER1’ (1300 292 371) provides advice and assistance to Australian individuals and organisations impacted by cybersecurity incidents. The Hotline is available 24 hours a day, seven days a week. Incident ResponseASD provides incident response services to all entities that have been compromised by malicious cyber actors. ASD prioritises deployment of specialised digital forensics and incident response services in response to incidents causing significant impact to Australia and/or incidents involving high harm actors. HuntASD proactively conducts cyberthreat hunt operations on important Australian networks to detect intrusions by sophisticated cyber actors. This service is offered to entities, including in support of events of national significance. In such cases, ASD is invited by the entity to conduct a hunt, and works in partnership with the entity for the duration of the hunt activity. National Exercise Program (NEP)The National Exercise Program (NEP) runs scalable and agile exercises to help participants validate and improve their cybersecurity arrangements. The NEP also runs cybersecurity training workshops for industry and government. ASD periodically runs large-scale exercises, such as AquaEx, described in Case Study 3. Cyber Incident Response Plan and Readiness ChecklistIn January 2022, the ACSC published a Cyber Incident Response Plan Template and Cyber Incident Response Readiness Checklist. These documents are designed to help entities develop a cyber incident response plan to support an effective incident response. |
Leadership and planning
|
From 1 January 2021 to 30 June 2022… 140 110 39 119 28% |
Chief Information Officer (CIO)/CISO, Information Technology Security Advisor (ITSA) forums and newsletterASD runs a number of forums annually for Commonwealth government CIOs and CISOs, as well as additional forums for ITSAs. A newsletter is also published for participants. The forums and newsletters bring together senior cybersecurity practitioners to discuss strategic cybersecurity matters, as well as technical topics and tools. During the reporting period, ASD provided updates on the Hardening Government IT Initiative (HGIT), the Critical Infrastructure and Systems of National Significance (CISoNS) reforms, Essential Eight Maturity Model updates, and ASD incident response activities. Lessons learned from the 2021 Tokyo Olympics and the 2021 Census were also provided by participating entities. Partnership ProgramThe ACSC Partnership Program enables a wide range of organisations to engage with the ACSC. Through the Partnership Program, ACSC provides technical advisories, sector-based threat intelligence, news and advice to enhance situational awareness, collaboration opportunities, and resilience-building activities. Privileged User Training (PUT)ASD provides in-person and online Privileged User Training (PUT) for ICT users who hold system privileges beyond that of a normal user. Privileged users are technical staff with duties and system access that enable them to adjust and maintain the configurations of ICT systems. The course provides an overview of best-practice cybersecurity, including mitigating cybersecurity incidents in privileged users’ day-to-day work. ASD’s PUT is intended for entities that don’t have the capacity or requirement to run in-house training for their privileged users. Entities may provide their own alternative. |
Cyber defence services
|
From 1 January 2021 to 30 June 2022… 28,000 20 million 70,000 |
Cyber Threat Intelligence Sharing (CTIS)In November 2021, ASD began operating the new CTIS platform. CTIS allows participating entities to share observable indicators of compromise (IOCs) at machine speed. Participating organisations can then use these IOCs to identify activity on their own networks. The CTIS platform also allows participating organisations to bi-directionally share IOCs observed on their own networks with other CTIS partners. Australian Protective Domain Name System (AUPDNS)The AUPDNS uses threat intelligence to build a block list of known and assessed malicious web domains. These domains are often used to distribute malware, as part of malicious command-and-control channels, or as part of a data-exfiltration channel. AUPDNS prevents devices on subscribed networks from accessing the malicious domains on the block list, thereby interrupting potential malicious activity, see Case Study 5. Domain Takedown ServiceThe Domain Takedown Service prevents malicious resources from being hosted on unsuspecting entities’ web domains. The service detects potentially malicious activity that is using subscribed entities’ web domains, verifies that this activity is malicious, and issues a takedown notification request to the Domain Host (i.e. the internet service that manages that domain). The majority of takedown notifications are automatically initiated within one minute of identification. |
[1] Under the PSPF maturity model, a ‘Managing’ maturity level means there has been ‘[c]omplete and effective implementation’ of a given aspect of the PSPF. An ‘Embedded’ maturity level means there has been ‘[c]omprehensive and effective implementation’ of that aspect of the PSPF.
[2] Recommended email security: Sender Policy Framework (SPF) and Domain-based Message Authentication Reporting and Conformance (DMARC).
[3] Recommended email encryption: Transport Layer Security (TLS) and Mail Transfer Agency Strict Transport Security (MTA-STS).
[4] Recommended web server encryption: Hypertext Transfer Protocol Security (HTTPS) and HTTP Strict Transport Security (HSTS).
